“Anyone who stops learning is old, whether at twenty or eighty. Anyone who keeps learning stays young. The greatest thing in life is to keep your mind young.” — Henry Ford
Monk and Inversions
DoS & DDoS: Denial-of-service attack
- A denial-of-service (DoS) attack is a security threat that occurs when an attacker makes it impossible for legitimate users to access computer systems, networks, services or other information technology (IT) resources.
- Attackers in these types of attacks typically flood web servers, systems or networks with traffic that overwhelms the victim's resources and makes it difficult or impossible for anyone else to access them.
- Restarting a system will usually fix an attack that crashes a server, but flooding attacks are more difficult to recover from. Recovering from a distributed DoS (DDoS) attack in which attack traffic comes from a large number of sources is even more difficult.
- DoS and DDoS attacks often take advantage of vulnerabilities in networking protocols and how they handle network traffic.
- For example, an attacker might overwhelm the service by transmitting many packets to a vulnerable network service from different Internet Protocol (IP) addresses.
Signs of a DoS attack
- Slower or otherwise degraded network performance that is particularly noticeable when trying to access a website or open files on the network;
- Inability to access a website
- More spam email than usual
Preventing a DoS attack
An enterprise that suspects a DoS attack is underway should contact its internet service provider (ISP) to determine whether slow performance or other indications are from an attack or some other factor. The ISP can reroute the malicious traffic to counter the attack. It can also use load balancers to mitigate the severity of the attack.
ISPs also have products that detect DoS attacks, as do some intrusion detection systems (IDSes), intrusion prevention systems (IPSes) and firewalls. Other strategies include contracting with a backup ISP and using cloud-based anti-DoS measures.
There have been instances where attackers have demanded payment from victims to end DoS or DDoS attacks, but financial profit is not usually the motive behind these attacks. In many cases, the attackers wish to harm the business or reputation of the organization or individual targeted in the attack.
Types of DoS attacks
DoS and DDoS attacks have a variety of methods of attack. Common types of denial-of-service attacks include the following:
Application layer. These attacks generate fake traffic to internet application servers, especially domain name system (DNS) servers or Hypertext Transfer Protocol (HTTP) servers. Some application layer DoS attacks flood the target servers with network data; others target the victim's application server or protocol, looking for vulnerabilities.
- Buffer overflow. This type of attack sends more traffic to a network resource than it was designed to handle.
- DNS amplification. In a DNS DoS attack, the attacker generates DNS requests that appear to have originated from an IP address in the targeted network and sends them to misconfigured DNS servers managed by third parties. The amplification occurs as the intermediate DNS servers respond to the fake DNS requests. The responses from intermediate DNS servers to the requests may contain more data than ordinary DNS responses, which requires more resources to process. This can result in legitimate users being denied access to the service.
- Ping of death. These attacks abuse the ping protocol by sending request messages with oversized payloads, causing the target systems to become overwhelmed, stop responding to legitimate requests for service and possibly crash the victim's systems.
- State exhaustion. These attacks -- also known as Transmission Control Protocol (TCP) attacks -- occur when an attacker targets the state tables held in firewalls, routers and other network devices and fills them with attack data. When these devices incorporate stateful inspection of network circuits, attackers may be able to fill the state tables by opening more TCP circuits than the victim's system can handle at once, preventing legitimate users from accessing the network resource.
- SYN flood. This attack abuses the TCP handshake protocol by which a client establishes a TCP connection with a server. In an SYN flood attack, the attacker directs a high-volume stream of requests to open TCP connections with the victim server with no intention of completing the circuits. A successful attack can deny legitimate users access to the targeted server.
- Teardrop. These attacks exploit flaws like how older operating systems (OSes) handled fragmented IP packets. The IP specification enables packet fragmentation when the packets are too large to be handled by intermediary routers, and it requires packet fragments to specify fragment offsets. In teardrop attacks, the fragment offsets are set to overlap each other. Hosts running affected OSes are then unable to reassemble the fragments, and the attack can crash the system.
- Volumetric. These DoS attacks use all the bandwidth available to reach network resources. To do this, attackers must direct a high volume of network traffic at the victim's systems. Volumetric DoS attacks flood a victim's devices with network packets using UDP or Internet Control Message Protocol (ICMP). These protocols require relatively little overhead to generate large volumes of traffic, while, at the same time, the victim's network devices are overwhelmed with network packets, trying to process the incoming malicious datagrams.
In a distributed denial-of-service attack, the attacker may use computers or other network-connected devices that have been infected by malware and made part of a botnet. DDoS attacks use command-and-control servers (C&C servers) to control the botnets that are part of the attack. The C&C servers dictate what kind of attack to launch, what types of data to transmit, and what systems or network connectivity resources to target with the attack.
A distributed denial-of-service (DDoS) attack is a malicious attempt to disrupt the normal traffic of a targeted server, service or network by overwhelming the target or its surrounding infrastructure with a flood of Internet traffic.
DDoS attacks achieve effectiveness by utilizing multiple compromised computer systems as sources of attack traffic. Exploited machines can include computers and other networked resources such as IoT devices.
From a high level, a DDoS attack is like an unexpected traffic jam clogging up the highway, preventing regular traffic from arriving at its destination.
How does a DDoS attack work?
DDoS attacks are carried out with networks of Internet-connected machines.
These networks consist of computers and other devices (such as IoT devices)which have been infected with malware, allowing them to be controlled remotely by an attacker. These individual devices are referred to as bots (or zombies), and a group of bots is called a botnet.
Once a botnet has been established, the attacker is able to direct an attack by sending remote instructions to each bot.
When a victim’s server or network is targeted by the botnet, each bot sends requests to the target’s IP address, potentially causing the server or network to become overwhelmed, resulting in a denial-of-service to normal traffic.
Because each bot is a legitimate Internet device, separating the attack traffic from normal traffic can be difficult.
How to identify a DDoS attack
The most obvious symptom of a DDoS attack is a site or service suddenly becoming slow or unavailable. But since a number of causes — such a legitimate spike in traffic — can create similar performance issues, further investigation is usually required. Traffic analytics tools can help you spot some of these telltale signs of a DDoS attack:
- Suspicious amounts of traffic originating from a single IP address or IP range
- A flood of traffic from users who share a single behavioral profile, such as device type, geolocation, or web browser version
- An unexplained surge in requests to a single page or endpoint
- Odd traffic patterns such as spikes at odd hours of the day or patterns that appear to be unnatural (e.g. a spike every 10 minutes)
There are other, more specific signs of DDoS attack that can vary depending on the type of attack.
What are some common types of DDoS attacks?
Different types of DDoS attacks target varying components of a network connection. In order to understand how different DDoS attacks work, it is necessary to know how a network connection is made.
A network connection on the Internet is composed of many different components or “layers”. Like building a house from the ground up, each layer in the model has a different purpose.
The OSI model, shown below, is a conceptual framework used to describe network connectivity in 7 distinct layers.

While nearly all DDoS attacks involve overwhelming a target device or network with traffic, attacks can be divided into three categories. An attacker may use one or more different attack vectors, or cycle attack vectors in response to counter measures taken by the target.
Application layer attacks
The goal of the attack:
Sometimes referred to as a layer 7 DDoS attack (in reference to the 7th layer of the OSI model), the goal of these attacks is to exhaust the target’s resources to create a denial-of-service.
The attacks target the layer where web pages are generated on the server and delivered in response to HTTP requests. A single HTTP request is computationally cheap to execute on the client side, but it can be expensive for the target server to respond to, as the server often loads multiple files and runs database queries in order to create a web page.
Layer 7 attacks are difficult to defend against, since it can be hard to differentiate malicious traffic from legitimate traffic.
Application layer attack example:
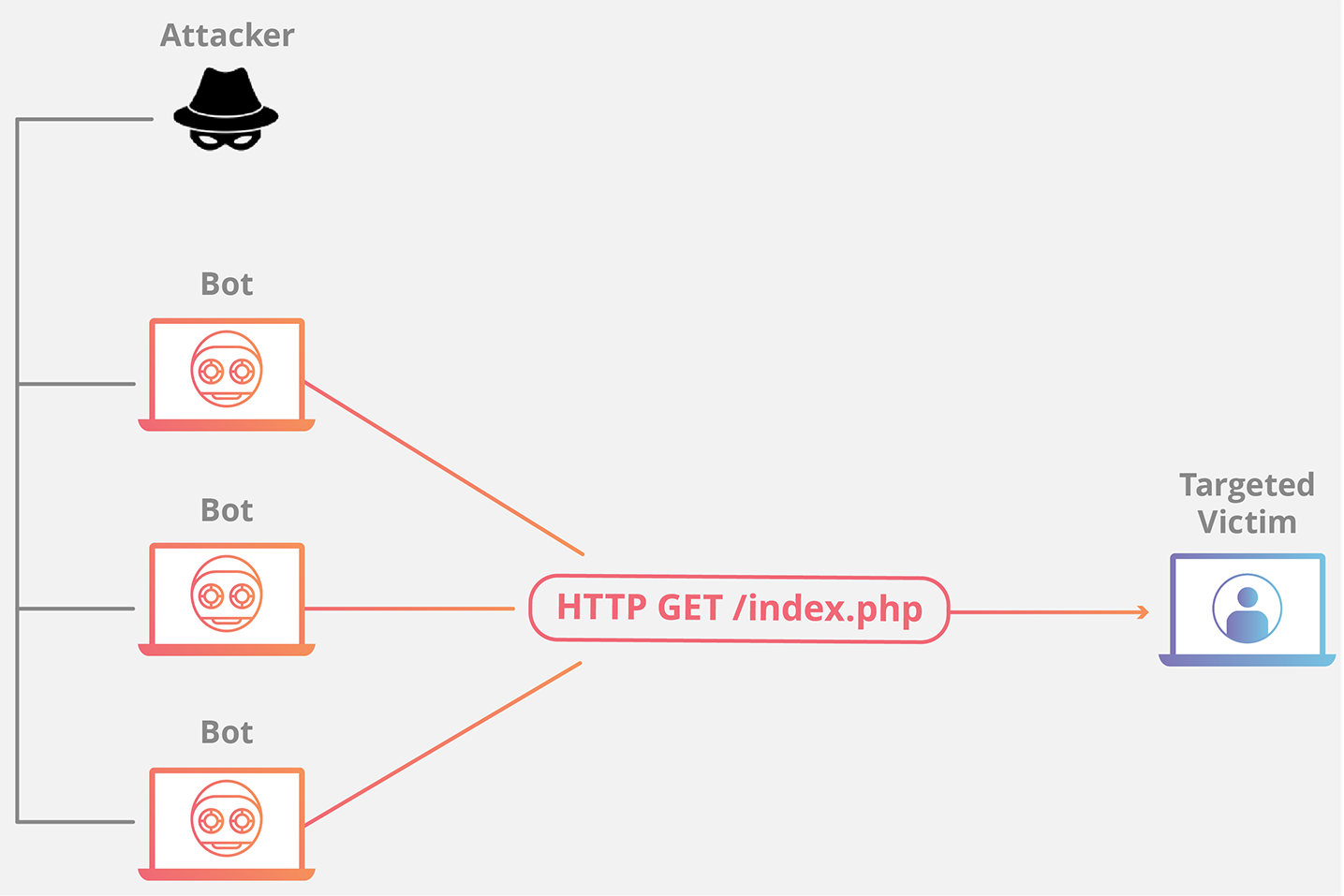
HTTP flood
This attack is similar to pressing refresh in a web browser over and over on many different computers at once – large numbers of HTTP requests flood the server, resulting in denial-of-service.
This type of attack ranges from simple to complex.
Simpler implementations may access one URL with the same range of attacking IP addresses, referrers and user agents. Complex versions may use a large number of attacking IP addresses, and target random urls using random referrers and user agents.
Protocol attacks
The goal of the attack:
Protocol attacks, also known as a state-exhaustion attacks, cause a service disruption by over-consuming server resources and/or the resources of network equipment like firewalls and load balancers.
Protocol attacks utilize weaknesses in layer 3 and layer 4 of the protocol stack to render the target inaccessible.
Protocol attack example:
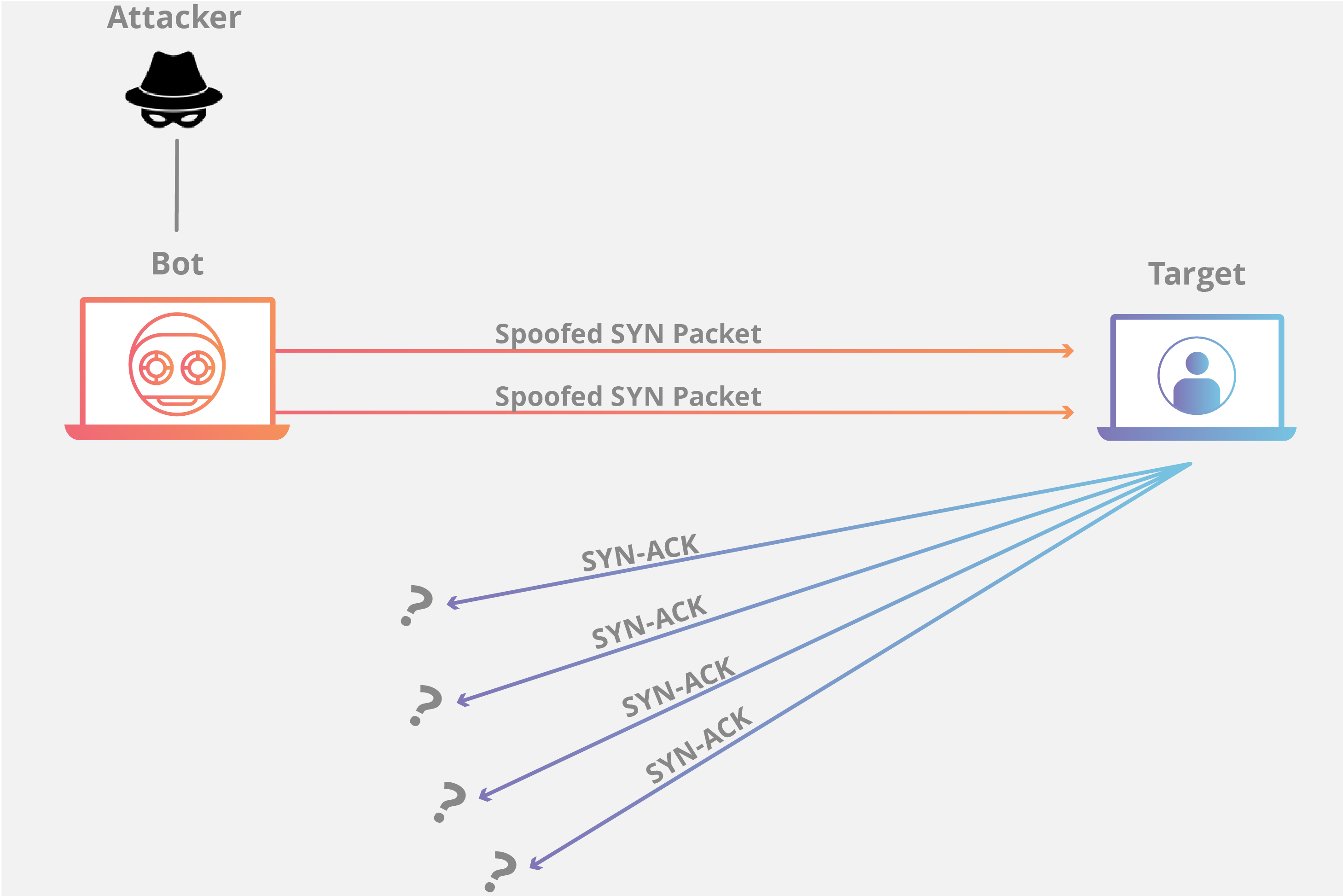
SYN flood
A SYN Flood is analogous to a worker in a supply room receiving requests from the front of the store.
The worker receives a request, goes and gets the package, and waits for confirmation before bringing the package out front. The worker then gets many more package requests without confirmation until they can’t carry any more packages, become overwhelmed, and requests start going unanswered.
This attack exploits the TCP handshake — the sequence of communications by which two computers initiate a network connection — by sending a target a large number of TCP “Initial Connection Request” SYN packets with spoofed source IP addresses.
The target machine responds to each connection request and then waits for the final step in the handshake, which never occurs, exhausting the target’s resources in the process.
Volumetric attacks
The goal of the attack:
This category of attacks attempts to create congestion by consuming all available bandwidth between the target and the larger Internet. Large amounts of data are sent to a target by using a form of amplification or another means of creating massive traffic, such as requests from a botnet.
Amplification example:
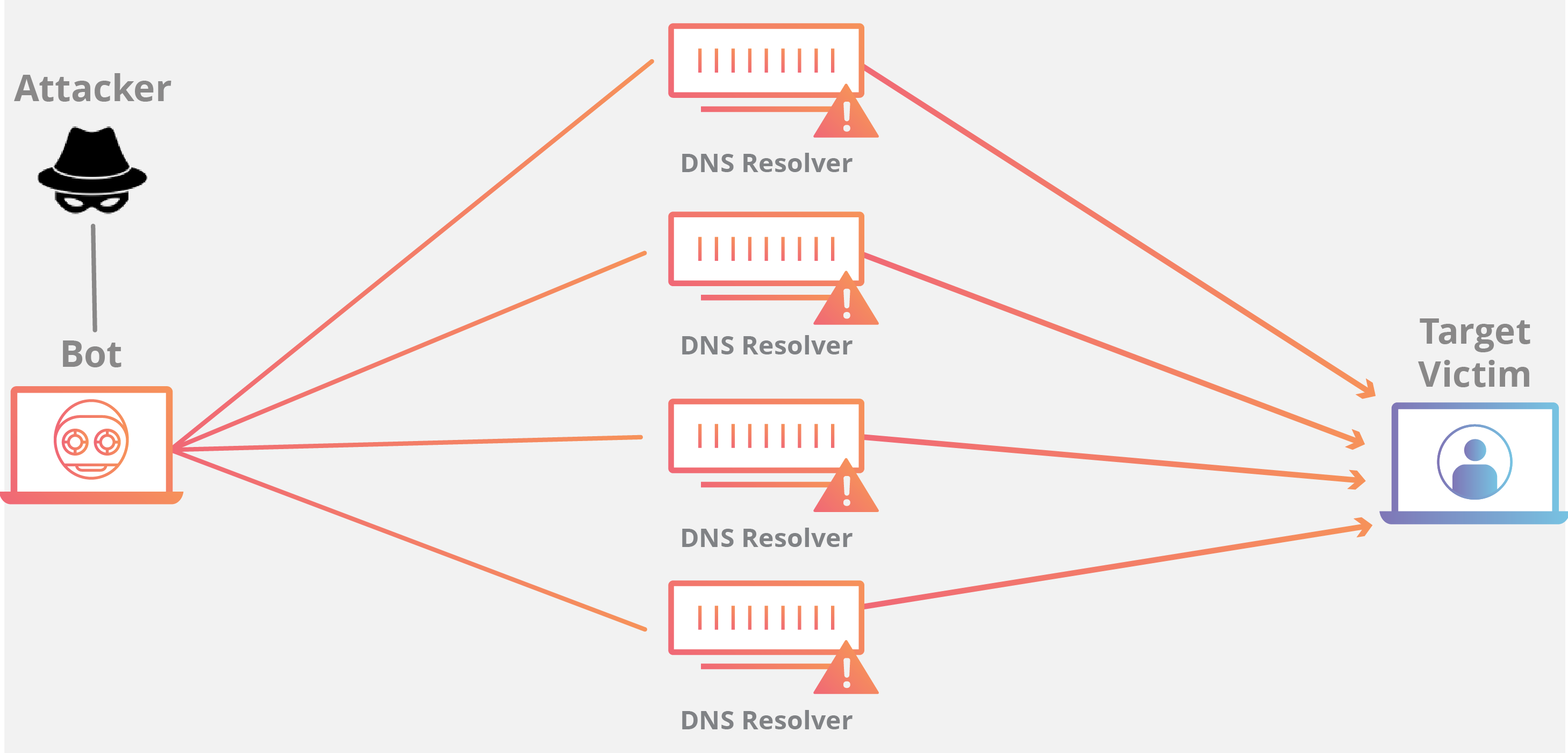
DNS Amplification
A DNS amplification is like if someone were to call a restaurant and say “I’ll have one of everything, please call me back and repeat my whole order,” where the callback number actually belongs to the victim. With very little effort, a long response is generated and sent to the victim.
By making a request to an open DNS server with a spoofed IP address (the IP address of the victim), the target IP address then receives a response from the server.
Batch Programming
Batch Programming
Batch file programming is a way of making a computer do things simply by creating a batch file.
Batch programming is a programming paradigm that can execute certain commands automatically at the level of an operating system such as DOS or Windows 7 / XP.
A batch file is a stack of such commands. If it is retrieved with the command line, the system will execute each task listed in succession.
Batch files are often used to control and configure operating systems, but can also be used for other operations such as server installations.
A batch file is a collection of instructions that are used to run multiple commands at a time. It is a bundle of packages that are written In a sequence so that the user does not have to put commands and instructions again and again. These files contain .bat extension. This means that you have to save the batch files by using the .bat extension at the end of the file name. These are DOS commands and also can run on command prompt.
Batch file function example: Program demonstrating function with return values
@echo OFF
CALL :retun_value_function ret_val1,ret_val2
ECHO The square root of %ret_val1% is %ret_val2%
PAUSE
EXIT /B %ERRORLEVEL%
:return_value_function
SET %~1=100
SET %~2=10
EXIT /B 0
@echo off
SETLOCAL
CALL :SetValue value1,value2
echo %value1%
echo %value2%
EXIT /B %ERRORLEVEL%
:SetValue
set "%~1 = 5"
set "%~2 = 10"
EXIT /B 0
Batch file function example: Program demonstrating function with parameters
@echo OFF
CALL :param_function 20, 400
EXIT /B %ERRORLEVEL%
:param_function
ECHO The square of %~1 is %~2
PAUSE
EXIT /B 0
http://www.trytoprogram.com/batch-file-for-loop/
Layered Architecture
By organizing code into layers, common low-level functionality can be reused throughout the application. This reuse is beneficial because it means less code needs to be written and because it can allow the application to standardize on a single implementation, following the don't repeat yourself (DRY) principle.
With a layered architecture, applications can enforce restrictions on which layers can communicate with other layers. This architecture helps to achieve encapsulation. When a layer is changed or replaced, only those layers that work with it should be impacted. By limiting which layers depend on which other layers, the impact of changes can be mitigated so that a single change doesn't impact the entire application.
Layers (and encapsulation) make it much easier to replace functionality within the application. For example, an application might initially use its own SQL Server database for persistence, but later could choose to use a cloud-based persistence strategy, or one behind a web API. If the application has properly encapsulated its persistence implementation within a logical layer, that SQL Server-specific layer could be replaced by a new one implementing the same public interface.
The most common organization of application logic into layers is shown in Figure 5-2.

Figure 5-2. Typical application layers.
ASP.NET Web API
The term API stands for “Application Programming Interface”. ASP.NET Web API is a framework, provided by Microsoft, which makes it easy to build Web APIs, i.e. HTTP based services. The ASP.NET Web API is an ideal platform for building Restful services on top of the .NET Framework. These Web API services can be consumed by a variety of clients such as
- Browsers
- Mobile applications
- Desktop applications
- IOTs, etc.
The most important thing to keep in mind is that we can develop both Restful and Non-Restful Web Services using the ASP.NET Web API framework. But mostly this framework is used to create RESTful services. In short, this framework does not provide any specific architectural style for creating the services.
REST stands for Representational State Transfer. This is an architectural pattern used for exchanging data over a distributed environment. In Rest, there is something called Client and Server, and the data can be exchanged between the client and server over a distributed environment. Distributed environment means the client can be on any platform like Java, .NET, PHP, etc. and the server can also be on any platform like Java, .NET, PHP, etc. The REST architectural pattern treats each service as a resource and a client can access those resources by using HTTP Protocol methods such as GET, POST, PUT, PATCH, and DELETE.
Here are the REST constraints.
1. Client-Server Constraint:
This is the first constraint. This constraint specifies that a Client sends a request to the server and the server sends a response back to the client. This separation of concerns supports the independent development of both client-side and server-side logic. That means client applications and server applications should be developed separately without any dependency on each other. A client should only know resource URIs and that’s all.
2. Stateless Constraint:
The next constraint is the Stateless Constraint. The stateless constraint specifies that the communication between the client and the server must be stateless between requests. That means the server should not be storing anything on the server related to the client. The request from the client should contain all the necessary information so that the server can identify the client and can process that request. This ensures that each request can be treated independently by the server.
3. Cacheable Constraint:
In real-time applications, some data provided by the server is not changed that frequently like the list of Countries, the list of States, the list of cities, and some master data. The Cacheable Constraint says that let the client know how long this data is good for so that the client does not have to come back to the server for that data over and over again.
4. Uniform Interface Constraint:
The Uniform Interface Constraint defines an interface between the client and the server. To understand the uniform interface constraint, first, we need to understand what a resource is and the HTTP verbs such as GET, PUT, POST, PATCH, and DELETE. In the context of a RESTFUL Service, resources typically represent data entities. The Product, Employee, Customer, Country, State, City, etc. are all resources. The HTTP verb (GET, PUT, POST, PATCH, and DELETE) that is sent with each request tells the API what to do with the resource. Each resource is identified by a specific URI (Uniform Resource Identifier).
5. Content Negotiation:
One of the constraints of the REST service is that the client should have the ability to decide in which format they want the response – whether they want the response in XML or JSON etc. This is called Content Negotiation
6. Layered System:
REST allows us to use a layered system architecture where we deploy the APIs in server A, store data on server B and authenticate requests in server C. For example, a client cannot ordinarily tell whether it is connected directly to the server or to an intermediary along the way.
HTTP Verbs or HTTP Methods
ASP.NET Web API
- It is a framework that helps us to develop HTTP Based services i.e. Restful Services.
- Web API is an open-source platform.
- It supports most of the MVC features which keep Web API over WCF.
if we want to expose our data (business data) to the browsers as well as to all these modern devices apps in a fast, secure and simple way, then we should have an API that should be compatible with browsers as well as all these modern devices.
The ASP.NET WEB API is a great framework for building HTTP services that can be consumed by a broad range of clients including browsers, mobiles, iPhones, and tablets.
Advantages of using ASP.NET Web API?
Using ASP.NET Web API has several advantages, but the core advantages are as follows:
- It supports all the HTTP features. That means you can use all the built-in HTTP Heapers such as Content-Type, Accept, Authorization, etc. and HTTP Status codes such as 500, 200, 404, etc. and HTTP verbs such as GET, POST, PUT, PATCH, and DELETE to perform CRUD operations
- It supports Attribute Routing which is good for SEO as well as user-friendly URLs.
- It supports content negotiation i.e. as per the client request, the server sends the response in that format (if possible). The Response generated in JSON or XML format using MediaTypeFormatter
- It can be hosted in IIS as well as self-host outside of IIS
- Supports Model Binding and Validation.
Monk and Inversions
using System; public class Solution { public static void Main () { int T = Convert . ToInt32 ( Console . ReadLine...
-
The software life cycle is a process that consists of a series of planned activities to develop or alter the Software Products. lt s use...
-
1. What is brute force attack? A brute force attack is a trial-and-error method used to obtain information such as a user password or pe...


