Suppose a process in host C has a UDP socket with port number 787. Suppose host A and host B each send a UDP segment to host C with destination port number 787. Will both of these segments be directed to the same socket at host C? If so, how will the process at host C know that these segments originated from two different hosts?
Yes, both the segments that are sent by Host A and Host B will be directed to the same socket at Host C because: Host C has a UDP socket with port number 789 & Both the hosts A and B use the same destination port number. The process at Host C can know the origins of the UDP segment. as For each received segment, at the socket interface, the IP addresses are provided by the operating system which determine the origins of the individual segments. Host C checks its datagram for its fields , it contains the four fields which gives the data and finds which socket is send those data
It has been said that when IPV6 tunnels through IPV4 routers , IPV6 treats the IPV4 tunnels as link layer protocols. Do you agree with this statement? Why or why not?
Explain the functions of storage area networks.
Discuss in detail about SAN architecture
- A SAN (storage area network) is a network of storage devices that can be accessed by multiple servers or computers, providing a shared pool of storage space.
- Each computer on the network can access storage on the SAN as though they were local disks connected directly to the computer.
What Is a Storage Area Network (SAN)?
- A Storage Area Network (SAN) is a specialized, high-speed network that provides block-level network access to storage.
- SANs are typically composed of hosts, switches, storage elements, and storage devices that are interconnected using a variety of technologies, topologies, and protocols. SANs may also span multiple sites.
- A SAN presents storage devices to a host such that the storage appears to be locally attached. This simplified presentation of storage to a host is accomplished through the use of different types of virtualization.
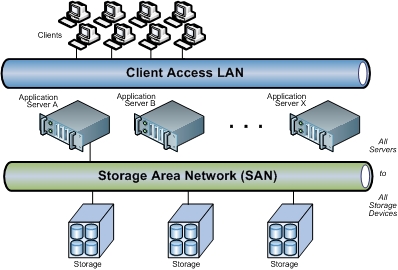
SANs are often used to:
- Improve application availability (e.g., multiple data paths)
- Enhance application performance (e.g., off-load storage functions, segregate networks, etc.)
- Increase storage utilization and effectiveness (e.g., consolidate storage resources, provide tiered storage, etc.), and improve data protection and security.
- SANs also typically play an important role in an organization's Business Continuity Management (BCM) activities.
SANs are commonly based on Fibre Channel (FC) technology that utilizes the Fibre Channel Protocol (FCP) for open systems and proprietary variants for mainframes. In addition, the use of Fibre Channel over Ethernet (FCoE) makes it possible to move FC traffic across existing high speed Ethernet infrastructures and converge storage and IP protocols onto a single cable. Other technologies like Internet Small Computing System Interface (iSCSI), commonly used in small and medium sized organizations as a less expensive alternative to FC, and InfiniBand, commonly used in high performance computing environments, can also be used. In addition, it is possible to use gateways to move data between different SAN technologies.
What is SNMP?Simple Network Management Protocol (SNMP) is a standard protocol used for the communication and management of network devices connected over an IP.
With a set of standards, SNMP collects data from different hardware and software, organizes them, and aids in network fault detection and analysis. Most of the network devices like routers, switches, firewalls, printers, servers, CCTV cameras, and wireless access points are SNMP-enabled, and they send the performance data for monitoring. Thus, SNMP an integral part of interoperability between both the monitored and the monitoring systems.
SNMP Protocol
SNMP protocol is an application layer protocol defined by the Internet Architecture Board in RFC1157. SNMP is used to exchange management information between network devices. It is one of the most common protocols used for network management. SNMP is part of the Transmission Control Protocol/Internet Protocol (TCP/IP) suite as defined by the Internet Engineering Task Force.
Organizations use SNMP to monitor and manage devices on a local area network (LAN) or wide area network (WAN). Most network devices in the market come bundled with SNMP agents. If not, some devices also allow network admins to install the agents.
How does SNMP work?
Traffic flows across your network from different sources. SNMP communicates with the whole network and the devices in it. As mentioned earlier, SNMP is preconfigured on devices, and once the protocol is enabled, the devices will store their performance stats. Each network server will have multiple MIB files. The device MIB files are queried to fetch the monitoring data. The working of SNMP revolves around its components, wherein each component contributes management of resources.
SNMP works by sending protocol data units, also known as SNMP GET requests, to network devices that respond to SNMP. All these communications are tracked, and network monitoring tools use them to fetch data from SNMP.
What are the components of SNMP?
The components of an SNMP-managed environment include an SNMP manager, its managed devices, an SNMP agent, and a management information base (MIB), all of which play a crucial role in its architecture.
SNMP manager
The SNMP manager is the central system used to monitor the SNMP network. Also known as a network management station (NMS), an SNMP manager is responsible for communicating with the SNMP-agent-implemented network devices. It runs on a host on the network. The manager queries the agents, gets responses, sets variables in them, and acknowledges events from them.
Managed devices
A managed device is an SNMP-enabled network entity that is managed by the SNMP manager. These are usually routers, switches, printers, or wireless devices.
SNMP agent
An SNMP agent is a software process that responds to SNMP queries to provide status and statistics about a network node. SNMP agents play the most important role in management. They are locally located and associated with SNMP network devices from which they collect, store, and transmit monitoring data. Data is transmitted to the designated SNMP manager when queried.
SNMP MIB
A management information base (MIB) forms an integral part of network management models.
An SNMP MIB is a structure that defines the format of information exchange in an SNMP system. Every SNMP agent maintains an information database describing the parameters of the device it manages. An SNMP manager is a software system that uses SNMP to collect data for fault management, performance management, and capacity planning. SNMP managers store collected data in a MIB as a commonly shared database between the agent and the manager. MIBs are saved as a text file in a specific format that MIB editors, SNMP agent builders, network management tools, and network simulation tools can understand, facilitating network building, testing, deployment, and operations. The managed objects in an MIB are called object identifiers (object IDs or OIDs).
SNMP OID
Object Identifiers (OIDs) are identifiable by strings of numbers separated by dots. There are two types of managed objects:
- Scalar: Objects defined by a single object instance (i.e. there can only be one result.)
- Tabular: Objects defined by multiple related object instances that are grouped in MIB tables.
MIBs organize OIDs hierarchically, which can be represented in a tree structure that has individual variable identifiers for each OID. This tree structure contains all the manageable features of all products arranged in it. Each branch of this tree has a number and a name, and each point is named after the complete path—from the top of the tree down—that leads to that point.
Basic SNMP Commands
- GET: A request sent by the SNMP manager to the managed device. Performing the GET command retrieves one or more values from the managed device.
- GET NEXT: Similar to the GET command, GET NEXT retrieves the value of the next OID in the MIB tree.
- GET BULK: Used to retrieve bulk data from a large MIB table.
- SET: Used by managers to modify or assign the value of the managed device.
- TRAPS: Unlike the above commands, which are initiated from the manager, the TRAPS command is initiated by agents. TRAPS is a signal sent to the manager by the agent when events occur.
- INFORM: Similar to TRAP in that it is initiated by the agent, but unlike TRAP, INFORM includes a confirmation from the manager once it receives the message.
State the additional capabilities of RMON2 over RMON1.
i. RMON1 only provides visibility into the data link and the physical layers; potential problems that occur at the higher layers still require other capture and decode tools.
ii. Because of RMON1's limitations, RMON2 was developed to extend functionality to upper-layer protocols. RMON2 provides full network visibility from the network layer through to the application layer.
iii. RMON2 is not a replacement for RMON1, but an extension of it. RMON2 extends RMON1 by adding nine more groups that provide visibility to the upper layers.
iv. With visibility into the upper-layer protocols, the network manager can monitor any upper-layer protocol traffic for any device or subnet in addition to the MAC layer traffic.
v. RMON2 allows the collection of statistics beyond a specific segment's MAC layer and provides an end-to-end view of network conversations per protocol.
vi. RMON2 is an extension of RMON that focuses on higher layers of traffic above the Medium Access Control (MAC) layer.
vii. RMON2 has an emphasis on IP traffic and application-level traffic. RMON2 allows network management applications to monitor packets on all network layers.
viii. This is difference from RMON which only allows network monitoring at MAC layer or below. RMON2 is intended to be used by network monitoring applications. It is not intended to be used by human.
ix. The network manager can view conversations at the network and application layers. Therefore, traffic generated by a specific host or even a specific application (for example, a Telnet client or a web browser) on that host can be observed.
x. Each monitored object must have a name, a syntax, an access-level, and an implementation-status. The name is used to identify the monitored object.
xi. The name has an object type and an object instance. Usually, the name is a text string for human to read. The syntax is the structure defined using ASN.1 notation. This abstract structure helps the human to understand the monitored object.
xii. The access-level means whether the monitored object can be read, written or both. Implementation-status is the status of the actual object. There are four possible values: mandatory, optional, obsolete, or deprecated.
What is the network ID portion of the IP address 191.154.25.66 if the default subnet
If the default subnet mask is used, then the network ID portion of the IP address 191.154.25.66 is 191.154.
The first octet, 191, indicates that this is a class B address, where the first two octets of the address represent the network portion. The default subnet mask for a Class B network address is 255.255.0.0. If a network administrator had implemented a subet mask other than the default, then the network portion of the address would be different. For example,an address of 191.154.25.66 with a subnet mask of 255.255.255.0 would have a network ID of 191.154.25
Your company has the network ID 165.121.0.0. You are responsible for creating subnets on the network, and each subnet must provide at least 900 host IDs.What subnet mask meets the requirement for the minimum number of host IDs and provides the greatest number of subnets?
A Class B address with a subnet mask of 255.255.252.0 creates 62 subnets with 1,022 hosts each. The next largest subnet creates 126 subnets, but each subnet contains only 510 hosts.
In binary format, the subnet mask reads as: 11111111 11111111 11111100 00000000. The third octet designates 1s for the first 6 digits. The 1s mask the subnet IDs. The calculation of the number of host IDs available for each subnet is based on the number of digits remaining in the network address after all of the subnets are created. To calculate the number of host IDs, raise 2 to the tenth power and then subtract 2. Note that there are two digits remaining in the third octet and eight digits in the fourth octet (00 00000000); these ten digits can be used to create host IDs.
The two host IDs that are subtracted are the two host IDs that contain all 0s and all 1s; those IDs identify the subnet itself and the broadcast address for all hosts on the subnet, respectively. The number of possible host IDs in each subnet ranges from 00 00000001 through 1111111110.
Converted to decimal notation, this range is 0.1 through 3.254.
For example, in the network 165.121.0.0/22, host addresses can range from 165.121.0.1 through 165.121.3.254
2016
Module 1
1.With a neat diagram, explain briefly about TCP/ IP Protocol graph.
- TCP/IP means Transmission Control Protocol and Internet Protocol.
- It is the network model used in the current Internet architecture as well.
- The entire IP suite -- a set of rules and procedures -- is commonly referred to as TCP/IP.
- TCP and IP are the two main protocols, though others are included in the suite.
- The TCP/IP protocol suite functions as an abstraction layer between internet applications and the routing and switching fabric.
- TCP/IP is more reliable than the OSI model.
Layers in TCP/IP Model
The TCP/IP Model has four layers:
1. Physical Layer and data link layer – combined known as host-to-network layer
2. Network layer
3. Transport
4. Application
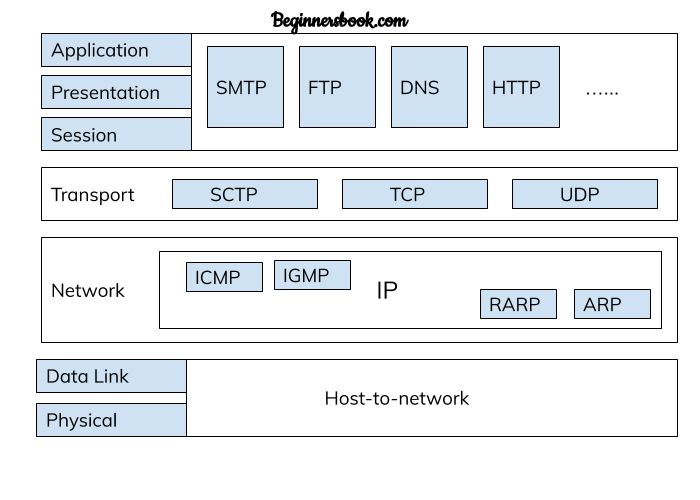
1. Physical and Data Link Layer
- Physical and Data Link Layers in TCP/IP model does not define any protocols, they support all the standard protocols.
- They are combined known as host-to-network layer. A network in TCP/IP internetwork can be LAN or WAN.
2. Network Layer
- In the network layer, the TCP/IP model supports internet working protocol in short known as IP.
- This layer is also known as the Internet layer.
- The main purpose of this layer is to organize or handle the movement of data on the
network.
- The IP uses four protocols internally: ARP, RARP, ICMP & IGMP.
3. Transport Layer
- Transport layer in TCP/Model can be represented by three protocols: Transmission control protocol (TCP), User data gram protocol (UDP) and Stream Control Transmission Protocol (SCTP).
- These three protocols in transport layer are responsible for delivery of messages from one process to another.
- The SCTP protocol was later introduced to meet the needs of newer applications.
4. Application Layer
- This is the top most layer of TCP/IP model.
- It is used for interaction between user and application.
- There are several protocols used by the application layer for user interaction such as: HTTP, SNMP, SMTP, DNS, TELNET, FTP etc.
2. What is OpenDNS? Explain the steps to set up OpenDNS on your home network.
OpenDNS
As we know, DNS server is to translate this human-readable web address (like www.yahoo.com ) into a computer-readable number also known as an IP address (209.131.36.158). Once your computer knows the IP location of a web domain name, it opens the website in your browser. But there are various drawbacks in the DNS server,
Suppose DNS server of your ISP is slow, the time it takes to resolve the web address adds up to the overall loading time of the website.
To solve this problem, we
look at a simple and reliable service called OpenDNS that speeds up
your Internet connection and also handles some other very important
issues.
OpenDNS is an American company providing Domain Name System (DNS) resolution services—with features such as phishing protection, optional content filtering, and DNS lookup in its DNS servers.
Setup
- There are no software to install, it’s very easy to set up and the price is just right - $0.
- To use OpenDNS, all you have to do is open your Network Connections or Router’s settings page and update the default DNS server to point to the OpenDNS nameservers that are 208.67.222.222 and 208.67.220.220.
- The whole process takes a few seconds but with this single step alone, you just made your computer safer and increased the overall browsing speed.
- Unlike the DNS servers of your less reliable ISP, OpenDNS servers store the IP addresses of millions of websites in their cache so it would take less time to resolve your requests. So if you have asked for an IP address of a website that has been previously requested by another OpenDNS user, you will get the reply instantly.
- Another huge advantage of using OpenDNS is that it blocks phishing websites from loading on your computer. It uses data from Phishtank, a community site that is also used by Yahoo! Mail to determine if some particular website is part of any online phishing scam.
- OpenDNS also takes care of any typos that you commit while typing the name of popular websites. For instance, if you type www.gogle.com omitting the additional “o” by mistake, OpenDNS will open the main www.google.com site automatically.
- If you are a parent worried about kids visiting adult websites on the home computer, you can configure OpenDNS to block any adult website from loading on the computer. In fact, quite a few business places use OpenDNS to block social sites like MySpace and Facebook on employee computers.
- Power users can assign abbreviations or OpenDNS Shortcuts to access their favourite websites more quickly.
4. Consider an HTTP client that wants to retrieve a Web document at a given
URL. The IP address of the HTTP server is initially unknown. What transport
and application-layer protocols besides HTTP are needed in this scenario?
- HTTP is an application layer protocol. HTTP needs TCP as its transport layer protocol.
- To establish a TCP connection, socket address of the server is needed. To perform this , another application layer protocol, DNS is used.
- DNS stands for Domain Name System. DNS uses UDP as its transport layer protocol.
- DNS is used to map url to IP address.
- Using DNS, client will get the IP address of the server.
- As HTTP is a standard application layer protocol, it has well known port number which is 80. This IP address + port number forms the socket address of the server.
- Now TCP connection will be established and HTTP request message will be send to server.
- Then server will respond with the web document.
Thus except HTTP, application layer protocol used is DNS & Transport layer protocols used are TCP and UDP.
5. i)From a user’s perspective, what is the difference between the download-
and-delete mode and the download-and-keep mode in POP3?
ii)Consider accessing your e-mail with POP3. Suppose you have configured your POP mail client to operate in the download-and-delete mode.
Complete the following transaction:
6. Classify each of the scenarios below as client-server, P2P, or hybrid, and
explain your answer briefly.
i) Amazon ii) Skype iii) BitTorrent iv) Telnet v) DNS vi) Whatsapp
Module 2
1. What are the duties of Transport Layer?
The basic function of the Transport layer is to accept data from the
layer above, split it up into smaller units, pass these data units to
the Network layer, and ensure that all the pieces arrive correctly at
the other end.
Functions of Transport Layer
- Service Point Addressing: Transport Layer header includes service point address which is port address. This layer gets the message to the correct process on the computer unlike Network Layer, which gets each packet to the correct computer.
- Segmentation and Reassembling: A message is divided into segments; each segment contains sequence number, which enables this layer in reassembling the message. Message is reassembled correctly upon arrival at the destination and replaces packets which were lost in transmission.
- Connection Control: It includes 2 types:
- Connectionless Transport Layer : Each segment is considered as an independent packet and delivered to the transport layer at the destination machine.
- Connection Oriented Transport Layer : Before delivering packets, connection is made with transport layer at the destination machine.
- Flow Control: In this layer, flow control is performed end to end.
- Error Control: Error Control is performed end to end in this layer to ensure that the complete message arrives at the receiving transport layer without any error. Error Correction is done through retransmission.
2. Why does FTP run on top of TCP rather than UDP? List the applications of UDp.
The protocols, such as HTTP, FTP, SMTP, and POP3, requires the application data to be received, without any gaps in the correct order.
• The TCP is more reliable than the UDP because TCP is a connected-oriented network where there is a guarantee of the transmitted packet in reaching the destination.
• UDP sends only the datagram and it does not stand in managing retransmission, data sequencing, or the connection.
• Here, to run on their data and for assured delivery, all the data streams want the reliable protocol.
• The packet loss or failures during the transmission cannot be decided in the UDP protocol.
The protocols named each of those are data stream and loss-free transport protocols.
• In TCP protocol, all the application data can be received without any gaps in a correct order but UDP does not.
• In TCP protocol, the data transmission is accurate.
• Also, the packet is delivered to the destination perfectly on the TCP protocol because it is a connected-oriented network.
• Thus, the loss of data in HTTP, SMTP, FTP and POP3cannot be affordable using the UDP protocol.
Therefore, the HTTP , FTP , SMTP , and POP3 run on top of the TCP protocol rather than on UDP protocol.
Numerous key Internet applications use UDP, including: the Domain Name System (DNS), where queries must be fast and only consist of a single request followed by a single reply packet, the Simple Network Management Protocol (SNMP), the Routing Information Protocol (RIP) and the Dynamic Host Configuration Protocol (DHCP).
3. Explain in detail about SCTP.
SCTP stands for Stream Control Transmission Protocol.
- It is a connection- oriented protocol in computer networks which provides a full-duplex association i.e., transmitting multiple streams of data between two end points at the same time that have established a connection in network.
- It is sometimes referred to as next generation TCP or TCPng.
- SCTP makes it easier to support telephonic conversation on Internet.
- A telephonic conversation requires transmitting of voice along with other data at the same time on both ends, SCTP protocol makes it easier to establish reliable connection.
- SCTP is also intended
to make it easier to establish connection over wireless network and
managing transmission of multimedia data.
Characteristics of SCTP :
- Unicast with Multiple properties – It is a point-to-point protocol which can use different paths to reach end host.
- Reliable Transmission – It uses SACK and checksums to detect damaged, corrupted, discarded, duplicate and reordered data. It is similar to TCP but SCTP is more efficient when it comes to reordering of data.
- Message oriented – Each message can be framed and we can keep order of datastream and tabs on structure. For this, In TCP, we need a different layer for abstraction.
- Multi-homing – It can establish multiple connection paths between two end points and does not need to rely on IP layer for resilience.
Advantages of SCTP :
- It is a full- duplex connection i.e. users can send and receive data simultaneously.
- It allows half- closed connections.
- The message’s boundaries are maintained and application doesn’t have to split messages.
- It has properties of both TCP and UDP protocol.
- It doesn’t rely on IP layer for resilience of paths.
Disadvantages of SCTP :
- One of key challenges is that it requires changes in transport stack on node.
- Applications need to be modified to use SCTP instead of TCP/UDP.
- Applications need to be modified to handle multiple simultaneous streams.
4. Suppose a process in host C has a UDP socket with port number 787. Suppose
host A and host B each send a UDP segment to host C with destination port
number 787. Will both of these segments be directed to the same socket at host
C? If so, how will the process at host C know that these segments originated
from two different hosts?
5. Consider sending a large file from one host to another over a TCP connection
that has no loss.
i) Suppose TCP uses AIMD for its congestion control without slow start.
Assuming CongWin increases by 1 MSS every time an ACK is received and
assuming approximately constant round-trip times, how long does it take for
CongWin to increase from 1 MSS to 5 MSS (assuming no loss events and
constant RTT)?
ii) What is the average throughput (in terms of MSS and RTT) for this
connection up through time 4 RTT?
a) It takes 1 RTT to increase CongWin to 1 MSS; 2 RTTs to increase to 2 MSS; 3 RTTs to increase to 3 MSS; 4 RTTs to increase to 4 MSS; 5 RTTs to increase to 5 MSS;
b) In the first RTT 1 MSS was sent; in the second RTT 2 MSS was sent; in the third RTT 3 MSS was sent; in the fourth RTT 4 MSS was sent. Thus, up to time 4 RTT, 1+2+3+4 = 10 MSS were sent (and acknowledged). Thus, we can say that the average throughput up to time 4 RTT was (10 MSS)/(4 RTT) = 2.5 MSS/RTT.
6. Host A and B are communicating over a TCP connection, and Host B has
already received from A all bytes up through byte 144. Suppose that Host A
then sends two segments to Host B back-to-back. The first and second
segments contain 20 and 40 bytes of data, respectively. In the first segment,
the sequence number is 145, source port number is 303, and the destination
port number is 80. Host B sends an acknowledgement whenever it receives a
segment from Host A.
i) In the second segment sent from Host A to B, what are the sequence number,
source port number, and destination port number?
ii) If the first segment arrives before the second segment, in the
acknowledgement of the first arriving segment, what is the acknowledgment
number, the source port number, and the destination port number?
iii) If the second segment arrives before the first segment, in the
acknowledgement of the first arriving segment, what is the acknowledgment
number?
iv) Suppose the two segments sent by A arrive in order at B. The first
acknowledgement is lost and the second segment arrives after the first timeout
interval.Draw a timing diagram, showing all other segments and
acknowledgements sent.
i) The first and second segments contain 20 and 40 bytes of data, respectively.
In the second segment sent from A to B, the sequence number is 165, the
source port number is 303, and the destination port number is 80.
ii) The first acknowledgment has acknowledgment number 165, source port
80, and destination port 303.
ii) The acknowledgment number will be 145, indicating that it is still waiting
for bytes 145 and onward.
iv) The sequence number of the retransmission is 145 and it carries 20 bytes of
data. The acknowledgment number of the additional acknowledgment is 205.
Module 3
1. write down the subnet address, broadcast address & valid host range for the ip address 10. 10. 10.5/20.
2. Elaborate about multicast routing protocols.
- Multicast routing is a method of transmitting to all subscribers registered in a group by one transmission unlike unicast routing (i.e. OSPF, RIP) which transmits 1: 1 necessary data.
- To implement the multicast routing, IGMP protocol and multicast routing protocol (Reverse-path forwarding, PIM-SM) for registration subscriber grouping and control traffic are required for multicast transmission.
- Regarding IP multicast, it is a technique for one-to-many communication over an IP network.
- IP multicast covers some part of common multicast routing protocol.
- IP multicast also describe IP multicast software (i.e. VideoLAN,qpimd – PIM Daemon for Quagga, GNU — PIM module for the Quagga Routing Suite, UFTP, etc.).
- The multicast routing is specific and broad range of protocols for layer-3 routing protocol for multicast feature and it is defined on overview of the Internet Multicast Routing Architecture RFC5110.
Routing mechanism
A multicast routing protocol is a mechanism for constructing a loop-free shortest path from a source host that sends data to the multiple destinations that receives the data. IPV4 uses Class D address (224.0.0.0 ~ 239.255.255.255)[2] IPv6 multicast provides the previous feature of IPV4 and a new IPv6 feature, allowing a host to send a single data stream to a subset of all hosts (group transmission) concurrently.[6] There are four types of Well-Known IPv6 Multicast address range : ff02::1: All IPv6 devices,•ff02::2: All IPv6 routers,•ff02::5: All OSPFv3 routers,•ff02::a: All EIGRP (IPv6) routers.[7]
3. Find the shortest path tree & the routing table for the routers AF,C,D,E & F using forward search link state algorithm.
4. What is the difference between routing and forwarding?
Forwarding – transfer of a packet from an incoming link to an outgoing link within a single router.
Routing involves all of a network’s routers, Determine the Paths from source to destination.
5. Compare & contrast link state and distance vector routing algorithm?
6. Consider the network shown below.Show the operation of Dijkstra’s (link-
state) algorithm for computing the least cost path from E to all destinations. What is the shortest path from E to B, and what is the cost of this path?
Module 4
1. Compare VoIP & VoLTE.
2. Discuss in detail about the relationship between ubiquitous computing and IoT.
3. Enunciate in detail about the working of VPN.
4. Define and give examples of distributed Computing systems.
5. What are the two types of loss anticipation schemes used in VoIP?
6. Consider the network below. Suppose that the remote host and server
communicate with the ESP protocol in tunnel mode.
i) An IP datagram emitted by the server and destined to the remote host will
have whose IP address for the source address and whose IP address for the
destination address?
ii) When this datagram arrives at the router, the router may or may not
transform it into another IP datagram. The IP datagram sent by the router will
have whose IP address for the source address and whose IP address for the
destination address?
Module 5
1. With a neat diagram, explain briefly about SNIA shared storage model.
The SNIA Shared Storage Model
Terms like "SAN" and "NAS" become loaded with artificial and sometimes arbitrary meaning in the absence of a single, simple model for shared storage architectures. The SNIA Technical Council has developed a framework that captures the functional layers and properties of a storage system, regardless of the underlying design, product, or installation.
Much like the OSI 7-layer model in conventional networking, the SNIA Shared Storage Model may be used to describe common storage architectures graphically, while exposing what services are provided, where interoperability is required, and the pros and cons of each potential architecture.
The model describes architectures, but it is not itself an architecture. You cannot buy it, or a system that it describes by specifying it in a bid, or a request for a bid. You cannot build it. The model does not represent any value judgments between the architectures it describes. Instead, the model makes it possible to compare architectures and to communicate about them in a common vocabulary
2. Discuss in detail about SAN deploynent strategies.
3. Explain about Fibre Channel Protocol Suite with a neat diagram.
4. List down the benefits of storage area networks
5. Discuss in detail about different SAN topologies.
6. Explain in detail about SNMP.
Moduel 6
1. List out the commands for the following:
(i) To trace the network path to ktu.edu.in
(ii) To display the IP address of ktu.edu.in
(iii) To scan open ports at ktu.edu.in
(iv) To display the existing routing table entries
tracepath ktu.edu.in or traceroute ktu.edu.in
ii.nslookup ktu.edu.in or host ktu.edu.in or dig ktu.edu.in
iii.nmap ktu.edu.in
iv.route or netstat –r
2. With a neat diagram, explain the design & configuration of your campus network.
3. In the diagram below, we have 2 individual networls (192.168.1.0 and 192.168.3.0, t
with subnet mask of 255.255.255.0). We also have a GATEWAY machine with 3
network cards. lst card is connected to 192-168.1.0, 2nd card is connected to
192.168.3.0, and the 3rd card is connected to the external world.
(i) Comrnand to mak€ 192. I 68.3. * accessible from 1 92. 1 68. I .
*
(ii) Command to make 192.168.1.* accessible from 192.168.3.*
(iii) Command to allow Internet Access (External World)
i.Make 192.168.3.* Accessible from 192.168.1.* Now we need to add a routing entry such that we are able to ping 192.168.3. series ip-addresses from 192.168.1. series.The common point we have is the GATEWAY machine.So, on each machine in 192.168.1.* network a default gateway will be added as shown belowroute add default gw 192.168.1.10 Now when 192.168.1.1 pings 192.168.3.1, it will go to the GATEWAY via 192.168.1.10 In GATEWAY, add the following routing entryroute add -net 192.168.3.0 netmask 255.255.255.0 gw 192.168.3.10 Now all the packets addressed to 192.168.3.* network will be forwarded via the 192.168.3.10 interface, which then delivers the packets to the addressed machine.
ii.Make 192.168.1.* Accessible from 192.168.3.* Now we need to add a routing entry such that we are able to ping 192.168.1. series ip-addresses from 192.168.3. series.The common point we have is the GATEWAY machine.So, on each machine in 192.168.3.* network a default gateway will be added as shown belowroute add default gw 192.168.3.10 Now when 192.168.1.1 pings 192.168.3.1, it will go to the GATEWAY via 192.168.1.10 In GATEWAY, add the following routing entryroute add -net 192.168.1.0 netmask 255.255.255.0 gw 192.168.1.10 Now all the packets addressed to 192.168.1.* network will be forwarded via the 192.168.1.10 interface, which then delivers the packets to the addressed machine.
ii.Allow Internet Access ( External World )In the previous two example, we have interconnected the 2 different networks Now we need to access the internet from these 2 different networks. For that, we can add a default routing ( when no routing rule matches ) to the 125.250.60.59 which is connected to the external world as followsroute add default gw 125.250.60.59
4. Write down the subnet, broadcast address and valid host range for the IP
address 172.16.10.5/ 25
Subnet : 172.16.10.0
Broadcast addr : 172.16.10.127
Host range : 172.16.10.1 – 172.16.10.126
5. You have been given the following info :
IP: 192.168.3.146 Netmask: 255.255.248.0 Gateway: 192.168.1.100 DNS:
8.8.4.4 and your NIC is named eth0 on you Linux.
List down the steps to temporarily connect the Linux machine to the Internet
from the terminal
The ifconfig command also allows to configure the network settings, but thechanges made in such a manner, will be reset to default when you restart yourmachine, so you can use them to temporarily configure the network for testingpurposes. For example, you can use the following command to specify theprimary IP address and netmask for the eth0 interface:sudo ifconfig eth0 192.168.3.202 netmask 255.255.248.0 upNow add the default Gateway (Set your default gateway) sudo route add default gw 10.1.1.1
6. Consider the following string of ASCII characters that were captured by
Wireshark when the browser sent an HTTP GET message (this is the ctual
content of an HTTP GET message). The characters <cr><lf> are carriage return
and line feed characters (that is, the italicized character string <cr> in the text
below represents the single carriage-return character that was contained at that
point in the HTTP header). Answer the following questions, indicating where in
the HTTP GET message below you find the answers.
GET /cs453/index.html HTTP/1.1<cr><lf>Host: gaia.cs.umass.edu
<cr><lf> User-Agent: Mozilla/5.0 (Windows;U; Windows NT 5.1; en-
US; rv:1.7.2) Gecko/20040804 Netscape/7.2 (ax) <cr><lf>
Accept:ext/xml,application/xml,application/xhtml+xml,text/html;q=0.9,te
xt/plain;q=0.8,image/png,application/*,*/*;q=0.5 <cr><lf>Accept-
Language: en-us,en;q=0.5..Accept-Encoding:zip,deflate<cr><lf>
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7..Keep-Alive:
300<cr><lf> Connection:keep-alive<cr><lf><cr><lf>
i) What is the URL of the document requested by the browser? Make sure
you give the hostname and the file name parts of the URL.
ii) What version of HTTP is the browser running?
iii) Is a Netscape or an Internet Explorer browser making the request?
iv) Is the browser requesting a non-persistent or a persistent connection?
v) What is the IP address of the computer on which the browser is running?
vi)What do the strings "application/*" and "*/*" signify in the Accept:
header?
Ans
i). The document request was http://gaia.cs.umass.edu/cs453/index.htmlThe Host : field indicates the server’s name and /cs453/index.html indicates thefile name.
ii) The browser is running HTTP version 1.1, as indicated just before the first<cr><lf> pair.
iii) A Netscape browser is making the request. The User-agent: field indicates“Mozilla,” which is a nickname for Netscape’s browser.
iv) The browser is requesting a persistent connection, as indicated by theConnection:keep-alive .
v) This is a trick question. This information is not contained in an HTTPmessage anywhere. So there is no way to tell this from looking at theexchange of HTTP messages alone. One would need information from the IPdatagrams (that carried the TCP segment that carried the HTTP GETvi) "*/*" indicating all media type
EXTRA
What is OpenDNS? Explain the steps to set up OpenDNS on your home network.
As we know, DNS server is to translate this human-readable web address (like www.yahoo.com)
into a computer-readable number also known as an IP address (209.131.36.158). Once your
computer knows the IP location of a web domain name, it opens the website in your browser.
But there are various drawbacks in the DNS server, so to solve this we make use of
OpenDNS.
OpenDNS that speeds up your Internet connection and also handles some other very
important issues.
Step up process:
There is no software to install, it’s very easy to set up.
To use OpenDNS, open our Network Connections or Router’s settings page and update the default DNS server to point to the OpenDNS nameservers that are 208.67.222.222 and 208.67.220.220.
Advantage:
Unlike the DNS servers of your less reliable ISP, OpenDNS servers store the IP addresses
of millions of websites in their cache so it would take less time to resolve your requests.
So if you have asked for an IP address of a website that has been previously requested by
another OpenDNS user, you will get the reply instantly.
Another huge advantage of using OpenDNS is that it blocks phishing websites from
loading on your computer. It uses data from Phishtank, a community site that is also used
by Yahoo! Mail to determine if some particular website is part of any online phishing
scam.
OpenDNS also takes care of any typos that you commit while typing the name of popular
websites. For instance, if you type www.gogle.com omitting the additional “o” by mistake, OpenDNS will open the main www.google.com site automatically.
If you are a parent worried about kids visiting adult websites on the home computer, you
can configure OpenDNS to block any adult website from loading on the computer.
In fact, quite a few business places use OpenDNS to block social sites like MySpace
and Facebook on employee computers.
Power users can assign abbreviations or OpenDNS Shortcuts to access their favourite
websites more quickly.
For instance, you can set “mail” as a shortcut for http://mail.google.com/ or something
like “a” for www.reallylongname.com - just type the shortcut to access the site.
A good alternative for browser-based bookmarks and it works across all computers
where you have logged in to your OpenDNS account.
Explain Briefly about HTTP with Non-Persistent and Persistent Connections.
Hypertext Transfer Protocol (HTTP) is an application-layer protocol for transmitting
hypermedia documents, such as HTML.
It was designed for communication between web browsers and web servers, but it can also be
used for other purposes.
HTTP follows a classical client-server model, with a client opening a connection to make a
request, then waiting until it receives a response.
However, the HTTP server maintains no information about the clients, and if the client asks for
the same object again, the server resends the object. Therefore, HTTP is called a stateless protocol.
HTTP can use both nonpersistent connections and persistent connections.
A nonpersistent connection is the one that is closed after the server sends the requested object to
the client. In other words, the connection is used exactly for one request and one response.
Nonpersistent connections are the default mode for HTTP/1.0
With persistent connections, the server leaves the TCP connection open after sending responses
and hence the subsequent requests and responses between the same client and server can be sent.
The server closes the connection only when it is not used for a certain configurable amount of
time. With persistent connections, the performance is improved by 20%. Persistent connections are the
default mode for HTTP/1.1.
Consider the figure below, where the server is sending a HTTP RESPONSE message back the client
Suppose the server-to-client HTTP RESPONSE message is the following:
HTTP/1.1 200 OK
Date: Sun, 09 Sep 2018 06:07:13 +0000
Server: Apache/2.2.3 (CentOS)
Last-Modified: Sun, 09 Sep 2018 06:11:53 +0000
ETag:17dc6-a5c-bf716880.
Content-Length: 95626
Keep-Alive: timeout=49, max=57
Connection: Keep-alive
Content-type: image/html
Answer the following questions:
i. Was the server able to send the document successfully? Explain
Yes, the document was received successfully as the response code is 200 OK
ii. What is the default mode of connection for HTTP protocol? Is the connection in the reply persistent or nonpersistent? Explain.
The connection is persistent.
iii. What is the type of file being sent by the server in response?
The file type the server is sending is image/html.
iv. What is the name of the server and its version?
The name and version of the server is Apache/2.2.3
v. What are the maximum number of requests and responses the server has allowed? What happens when the maximum number of requests and responses are sent?
vi. What is the ETag in the success response message sent? State its significance.
The Etag is a string that uniquely identifies a resource. If a resource is updated, the Etag will change.
Explain in detail about the congestion control mechanisms in TCP
What are the duties of Transport Layer?
Transport Layer is the second layer of the TCP/IP model. It is an end-to-end layer used to deliver
messages to a host. The standard protocols used by Transport Layer are TCP(Transmission
Control Protocol), UDP( User Datagram Protocol), DCCP( Datagram Congestion Control
Protocol) etc.
End-to-end delivery- The transport layer transmits the entire message to the destination.
Therefore, it ensures the end-to-end delivery of an entire message from a source to the destination.
Addressing- The transport layer provides the user address which is specified as a station or port.
The port variable represents a particular TS-user of a specified station known as a Transport
Service access point (TSAP). Each station has only one transport entity. The transport layer
protocols need to know which upper-layer protocols are communicating.
Reliable delivery- The transport layer provides reliability services by retransmitting the lost and
damaged packets. The primary role of reliability is Error Control. In reality, no transmission
will be 100 percent error-free delivery. Therefore, transport layer protocols are designed to
provide error-free transmission.
Flow control- The transport layer is responsible for flow control. It uses the sliding window
protocol that makes the data transmission more efficient as well as it controls the flow of data so
that the receiver does not become overwhelmed. Sliding window protocol is byte-oriented rather
than frame oriented.
Multiplexing- the transport layer uses the multiplexing to improve transmission efficiency.
Explain in detail about Web Caching.
Web caching is the activity of storing data for reuse, such as a copy of a web page served by a
web server.
It is cached or stored the first time a user visits the page and the next time a user requests the
same page, a cache will serve the copy, which helps keep the origin server from getting overloaded.
Web caching solutions and strategies enhance page delivery speed significantly and reduce the
work needed to be done by the backend server.
Caching servers can be set to refresh at specific intervals or in response to certain events to
ensure that the freshest content is cached (useful for rapidly changing information, such as
breaking news or rapidly changing pricing).
Caching can also protect against total outages, delivering already cached content when servers are
down.
Explain in detail about FTP,SMTP, & HTTP
FTP
FTP stands for File transfer protocol.
FTP is a standard internet protocol provided by TCP/IP used for transmitting the files from one host to another.
It is mainly used for transferring the web page files from their creator to the computer that acts as a server for other computers on the internet.
It is also used for downloading the files to the computer from other servers.
Features:
It provides the sharing of files.
It is used to encourage the use of remote computers.
It transfers the data more reliably and efficiently.
Advantages of FTP:
Speed: The FTP is one of the fastest way to transfer the files from one computer to another
computer.
Efficient: It is more efficient as we do not need to complete all the operations to get the entire file.
Security: To access the FTP server, we need to login with the username and password. Therefore,
we can say that FTP is more secure.
Back & forth movement: FTP allows us to transfer the files back and forth. Suppose you are a
manager of the company, you send some information to all the employees, and they all send
information back on the same server.
Disadvantages of FTP:
The standard requirement of the industry is that all the FTP transmissions should be encrypted.
However, not all the FTP providers are equal and not all the providers offer encryption. So, we will
have to look out for the FTP providers that provides encryption.
FTP serves two operations, i.e., to send and receive large files on a network. However, the size
limit of the file is 2GB that can be sent. It also doesn't allow you to run simultaneous transfers to
multiple receivers.
Passwords and file contents are sent in clear text that allows unwanted eavesdropping. So, it is
quite possible that attackers can carry out the brute force attack by trying to guess the FTP
password.
It is not compatible with every system.
SMTP
SMTP stands for Simple Mail Transfer Protocol.
SMTP is a set of communication guidelines that allow software to transmit an electronic mail over
the internet is called Simple Mail Transfer Protocol.
It is a program used for sending messages to other computer users based on e-mail addresses.
It provides a mail exchange between users on the same or different computers, and it also supports:
It can send a single message to one or more recipients.
Sending message can include text, voice, video or graphics.
It can also send the messages on networks outside the internet.
The main purpose of SMTP is used to set up communication rules between servers. The servers
have a way of identifying themselves and announcing what kind of communication they are trying
to perform. They also have a way of handling the errors such as incorrect email address.
For example, if the recipient address is wrong, then receiving server reply with an error message of
some kind.
Hypertext Transfer Protocol (HTTP) is an application-layer protocol for transmitting hypermedia
documents, such as HTML.
It was designed for communication between web browsers and web servers, but it can also
be used for other purposes.
HTTP follows a classical client-server model, with a client opening a connection to make a
request, then waiting until it receives a response.
However, the HTTP server maintains no information about the clients, and if the client
asks for the same object again, the server resends the object. Therefore, HTTP is called a
stateless protocol.
HTTP can use both nonpersistent connections and persistent connections.
Write Short notes on Multiplexing and Demultiplexing in Transport Layer
TCP/IP means Transmission Control Protocol and Internet Protocol which is used in the network model.
Most communication in TCP/IP takes the form of exchanges of information between a program running
on one device, to a program on another device. Each instance of an application represents a copy of that
application software that needs to send and receive information. These application instances are
commonly called processes.
Multiplexing -
At the sender site, there may be many processes that want to send their packets. TCP at the transport layer
accepts all these messages from different sockets differentiated by their port numbers and after adding
headers, passes the segment to the network layer. This process is termed as Multiplexing.
Demultiplexing - At the receiver side, the TCP at transport layer accepts datagrams from the network
layer, removes IP header, checks their port numbers and then delivers the datagrams to the respective
sockets and ultimately to the attached processes. This process is referred to as Demultiplexing.
