- File transfer protocol (FTP) is a set of rules that computers follow for the transferring of files from one system to another over the internet.
- It may be used by a business to transfer files from one computer system to another, or websites may use FTP to upload or download files from a website's server.
- FTP uses two parallel TCP connections to transfer a file, a control connection and a data connection.
- The control connection is used for sending control information between the two hosts—information such as user identification, password, commands to change remote directory, and commands to “put” and “get” files.
- The data connection is used to actually send a file.
- Because FTP uses a separate control connection, FTP is said to send its control information out-of-band.
- Throughout a session, the FTP server must maintain state about the user.
Advantages of using FTP
- It allows you to transfer multiple files and folders.
- When the connection is lost then it has the ability to resume the transfer.
- There is no limitation on the size of the file to be transferred. The browsers allow a transfer of only up to 2 GB.
- Many FTP clients like FileZilla have the ability to schedule the transfers.
- The data transfer is faster than HTTP.
- The items that are to be uploaded or downloaded are added to the ‘queue’. The FTP client can add items to the ‘queue’.
Disadvantages of using FTP
- FTP doesn't encrypt the traffic so usernames, passwords, and other data can easily be read by capturing the data packets because while transferring as they are sent in cleartext. FTP is vulnerable to packet capture and other attacks.
SMTP (Simple Mail Transfer Protocol)
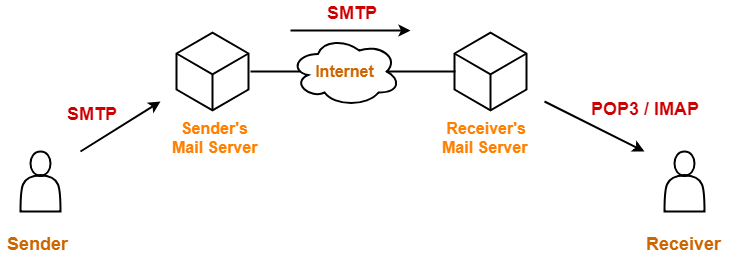
- SMTP is the heart of Internet electronic mail.
- SMTP transfers messages from senders’ mail servers to the recipients’ mail servers.
- SMTP is much older than HTTP
- It is used for sending the emails efficiently and reliably over the internet.
SMTP is a pure text based protocol.
- SMTP can only handle the messages containing 7 bit ASCII text.
- SMTP can not transfer other types of data like images, video, audio etc.
- SMTP can not transfer executable files and binary objects.
- SMTP can not transfer the text data of other languages like French, Japanese, Chinese etc.
MIME extends the limited capabilities of email.
As the name suggests,
- Multipurpose Internet Email Extension (MIME) is an extension to the internet email protocol.
- It extends the limited capabilities of email by enabling the users to send and receive graphics, audio files, video files etc in the message.
- MIME was specially designed for SMTP.
SMTP is a stateless protocol.
This is because-
- It does not maintain the state of its clients.
- If an email is asked to be sent twice, then SMTP server resends it without saying that the email has already been sent.
We can not use SMTP at the receiver’s side.
This is because-
- SMTP is a push protocol.
- At receiver’s side, a pull protocol like POP3, IMAP is needed.
- Receiver periodically checks if he has any mail from his mail server
NOTE-
To receive or download the email,
- Another protocol is needed between the receiver’s mail server and the receiver.
- The most commonly used protocols are POP3 and IMAP.
POP3 (Post Office Protocol)
- POP3 is an extremely simple mail access protocol.which is short and quite readable. Because the protocol is so simple, its functionality is rather limited.
- POP3 begins when the user agent (the client) opens a TCP connection to the mail server (the server) on port 110.
- With the TCP connection established, POP3 progresses through three phases: authorization, transaction, and update.
- During the first phase, authorization, the user agent sends a username and a password
(in the clear) to authenticate the user. - During the second phase, transaction, the user agent retrieves messages; also during this phase, the user agent can mark messages for deletion, remove deletion marks, and obtain mail statistics.
- The
third phase, update, occurs after the client has issued the quit
command, ending the POP3 session; at this time, the mail server deletes
the messages that were marked for
deletion.
- In a POP3 transaction, the user agent issues commands, and the server responds
to each command with a reply. - There
are two possible responses: +OK (sometimes followed by server-to-client
data), used by the server to indicate that the previous command was
fine; and -ERR, used by the server to indicate that something was wrong
with the previous command.
- The authorization phase has two principal commands: user <username> and
pass <password>. - Suppose that mailServer is the name of your mail server. You will see something like: telnet mailServer 110
+OK POP3 server ready
user bob
+OK
pass hungry
+OK user successfully logged on
If you misspell a command, the POP3 server will reply with an -ERR message.
- A user agent using POP3 can often be configured (by the user) to “download and delete” or to “download and keep.”
- The sequence of commands issued by a POP3 user agent depends on which of these two modes the user agent is operating in.
- In the download-and-delete mode, the user agent will issue the list, retr, and dele commands. The user agent then retrieves and deletes each message from the server.
- In the download-and- keep mode, the user agent leaves the messages on the mail server after downloading them.
- During a POP3 session between a user agent and the mail server, the POP3
server maintains some state information; in particular, it keeps track of which user
messages have been marked deleted. However, the POP3 server does not carry state
information across POP3 sessions. This lack of state information across sessions
greatly simplifies the implementation of a POP3 server.
IMAP
- IMAP is a mail access protocol. It has many more features than POP3, but it is also significantly more complex.
- Note that, unlike POP3, an IMAP server maintains user state information
across IMAP sessions - Another important feature of IMAP is that it has commands that permit a user
agent to obtain components of messages.
- MIME stands for Multipurpose Internet Mail Extensions.
- It is used to extend the capabilities of Internet e-mail protocols such as SMTP.
- The MIME protocol allows the users to exchange various types of digital content such as pictures, audio, video, and various types of documents and files in the e-mail.
- MIME is an e-mail extension protocol, i.e., it does not operate independently, but it helps to extend the capabilities of e-mail in collaboration with other protocols such as SMTP.
Need of MIME Protocol
MIME protocol is used to transfer e-mail in the computer network for the following reasons:
- The MIME protocol supports multiple languages in e-mail, such as Hindi, French, Japanese, Chinese, etc.
- Simple protocols can reject mail that exceeds a certain size, but there is no word limit in MIME.
- Images, audio, and video cannot be sent using simple e-mail protocols such as SMTP. These require MIME protocol.
- Many times, emails are designed using code such as HTML and CSS, they are mainly used by companies for marketing their product. This type of code uses MIME to send email created from HTML and CSS.
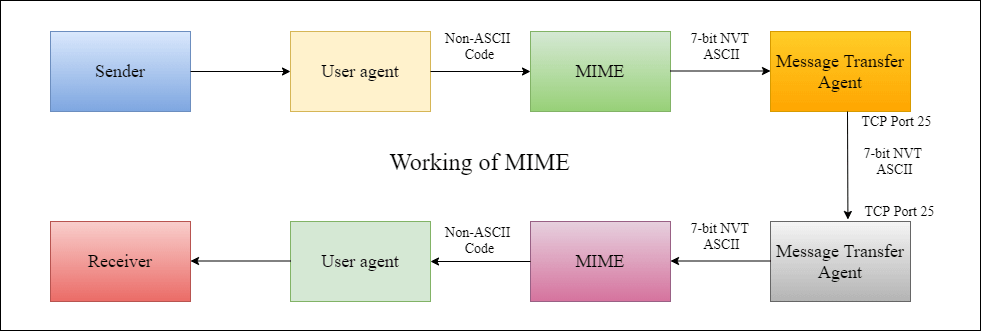
Working of MIME –
Suppose a user wants to send an
email through user agent and it is in a non-ASCII format so there is a
MIME protocol which converts it into 7-bit NVT ASCII format. Message is
transferred through e-mail system to the other side in 7-bit format now
MIME protocol again converts it back into non-ASCII code and now the
user agent of receiver side reads it and then information is finally
read by the receiver. MIME header is basically inserted at the beginning
of any e-mail transfer.
MIME Header:
It is added to the original e-mail header section to define transformation. There are five headers which we add to the original header:
- MIME Version – Defines version of MIME protocol. It must have the parameter Value 1.0, which indicates that message is formatted using MIME.
- Content Type – Type of data used in the body of message. They are of different types like text data (plain, HTML), audio content or video content.
- Content Type Encoding – It defines the method used for encoding the message. Like 7-bit encoding, 8-bit encoding, etc.
- Content Id – It is used for uniquely identifying the message.
- Content description – It defines whether the body is actually image, video or audio.